Decryption From Ransomware Viruses
Decryption From Ransomware Viruses
Northwind Data Recovery, a TRUSTED member of EUROPOL'S NoMoreRansom Project,
No more Ransom project has been fighting Ransomware since 2016.
In our Blog, we post every week news about ransomware found, decrypt, solved. As well as the solutions we have found for each of them in order to have access to them.
In recent years there is a rise of infections by viruses called Ransomware Viruses (dharma, Jigsaw, Scarab, Gandcrab, Matrix, Screenlocker, Cerber, HiddenTear, Locky, WannaCry, STOP), which are also known with different names such as Cryptolocker (and their variations like the Cryptowall, Troldesh, Locky and others).
GENERAL INFO ABOUT
Decryption From Ransomware Viruses
The way they work is pretty much common:
The computer is infected by the virus (usually by a misleading e-mail asking to click on a link, or by visiting untrustworthy websites), which encrypts the data with AES256 encryption and sends the key to the attacker. As a result, the files become non-functional, with weird file extensions (e.g. Scan001.locky or generally scan001.jpg.*) and it is impossible to be used.
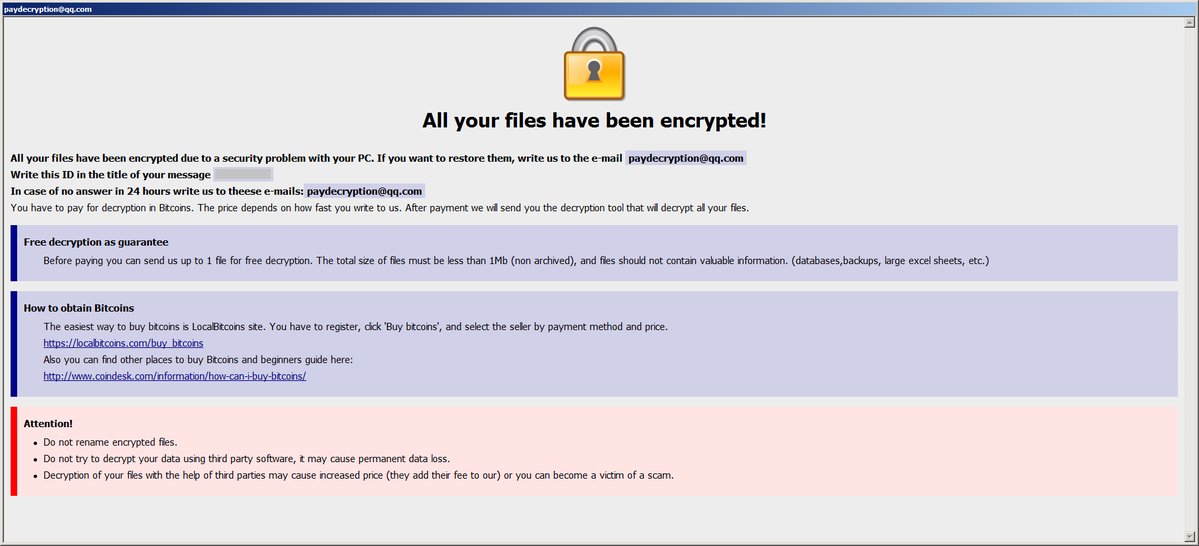
Then, the virus creates a message screen that informs the user, that his hard disk's data have been encrypted and ransom is asked to be paid, in order to be given the key for the data decryption. Usually the ransom is paid by bitcoin and the whole process is done via Tor networks, so it would not be possible to trace the attackers.
It is important to mention, that even if the asked ransom is paid, there is no guarantee that the attackers will give up the decryption key.
Also, it is worth mentioning that the original version of the virus was only targeting Windows Servers (most commonly versions 2003 and earlier), which had Windows Remote Desktop enabled at the default port (3389). The attackers exploited a security vulnerability of this software, installed the virus, encrypted the data by generating a random 128bit key, which they sent to themselves, and then deleted it from the hard drive by sdelete, so the trace of it would not be recoverable.
Later, the virus evolved with 256bit encryption and with non local storage of the key, so the decryption of the data would be impossible.
We have to point out, that the virus targets all local hard drives of the computer, but also the external and network ones connected at the time. Generally it targetsall disks that have a disk letter assigned (C:, D:, X: etc)
How CryptoViruses work:
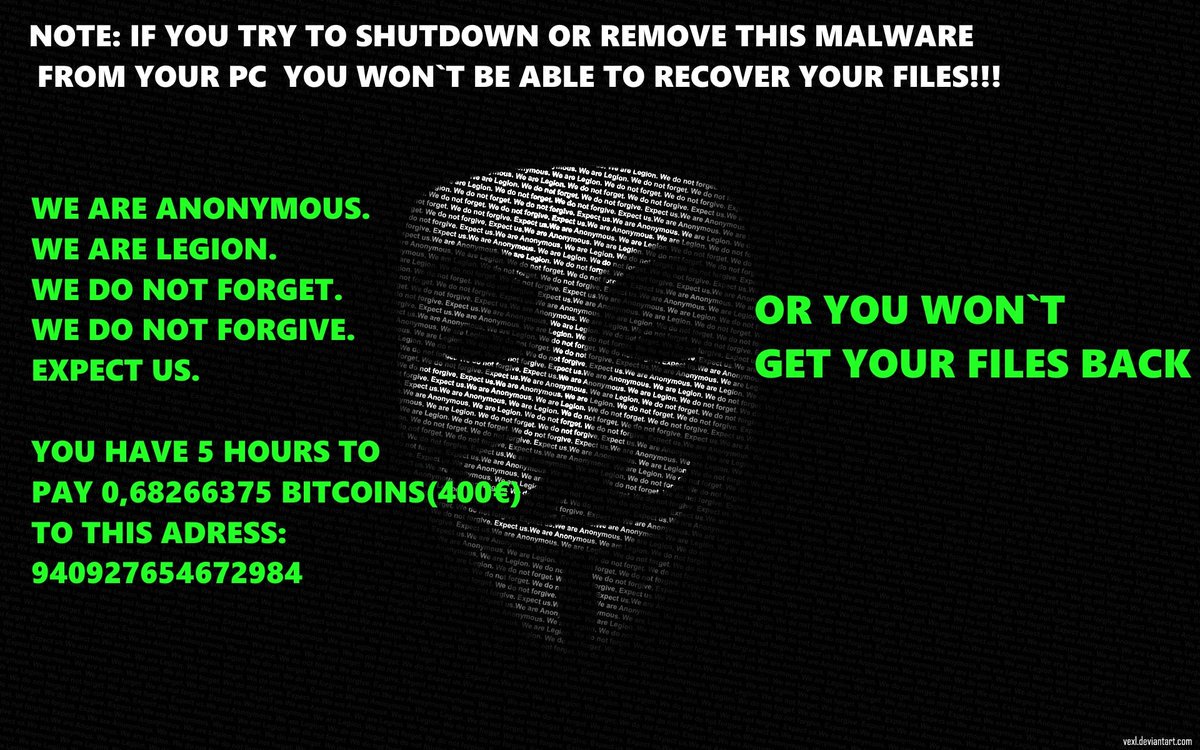
1. A computer gets infected by clicking on links or attachments in emails or through websites.The virus is then install on attacked computer. No user approval is asked for this action.
2. Virus will connect to the attacker's server and request a public RSA key. Public RSA key can be used to encrypt something but not to decrypt it.
3. Virus will generate an AES key (sometimes for each attacked file separately) and encrypt attacked file content using AES encryption. Original file is then deleted.
4. AES key is encrypted with the public RSA key and stored somewhere in the encrypted copy of attacked file.
5. The virus informs the victim about the problem and requests ransom for the decryption.
The problem:
Without the private RSA key from the attacker's server, it is impossible to decrypt AES keys and thus impossible to decrypt the data.
The solution:
The only way to decrypt the data is to get the private RSA keys and currently there are two options for that:
1. Pay the ransom. The result is not guaranteed, of course, and also paying ransom will help spreading the problem by creating other similar viruses.
2. Wait “Somehow” those private RSA keys may be obtained and the decryption may become possible. There is no guarantee such a thing will happen. There are sometimes glitches in the way the ransomware has been programmed, however the detection and reverse engineering of them takes a lot of time.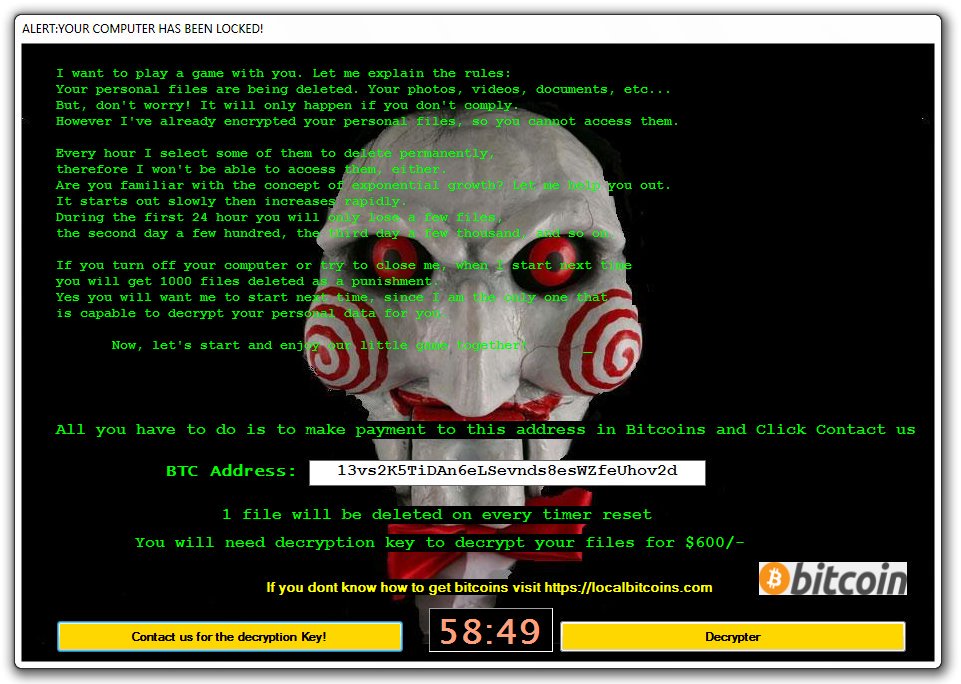 Currently, there are hunderds of variations of these viruses more sophisticated and very oftenly unbreakable. It is possible, for someone with zero programming skills, to purchase ready made ransomware kits, modify them easily and then spread them around hoping to catch unaware victims and demand ransom.
Currently, there are hunderds of variations of these viruses more sophisticated and very oftenly unbreakable. It is possible, for someone with zero programming skills, to purchase ready made ransomware kits, modify them easily and then spread them around hoping to catch unaware victims and demand ransom.
We, at Northwind Data Recovery, have skilled software engineers who participated in global forums in finding vulnarabilities in the ransomware coding and manipulate them in order to decrypt people's data.
In order to find out if we can help you decrypt your data, follow these instructions:
1. Send us an email with 2-3 encrypted files
2. In that email, include the ransom note. Usually this is a .txt or .html file with name like help_decrypt.txt or +decrypt_files.txt or similar. You can find it usually inside every folder with encrypted files.
3. If possible, send us a pair of encrypted and unencrypted files (which you may possibly have from an older backup)
4. Do not send us modified / corrupted files from various attempts you may have done.
A specialized technician will contact you with the results of the analysis and the evalution of the files you sent.



